What is Fast Flux?
Fast flux is a technique used mostly by cybercriminal to enhance the resilience of their infrastructure and make it harder to blocklist their actual IP address. This technique is majorly used to keep the uptime of the network high to avoid losses in revenue. In general, fast flux is used in phishing and scam campaigns, and at times in illegal gambling as well.
What is DNS and why is it important?
TIPFeel free to skip to the next section if you already know how DNS works
To understand Fast Flux we first need to understand how DNS (Domain name system) works. DNS is the phonebook of the internet. It acts as a way to connect your web browser to the world wide internet. Whenever you make a request from your browser the DNS server acknowledges this request and send the corresponding IP address associated with the requested website. So for example if you request www.google.com from your browser, the DNS server will send back 142.251.188.139 for IPv4 and/or 2607:f8b0:400e:c06::8b for IPv6 requests.
Now the whole DNS architecture works is a hierarchical patter and is divided mainly into 4 major types
- Recursive DNS
- Root nameserver
- TLD (top level domain) nameserver
- Authoritative nameserver
Image (source: Cloudflare) below shows the DNS architecture hierarchy.
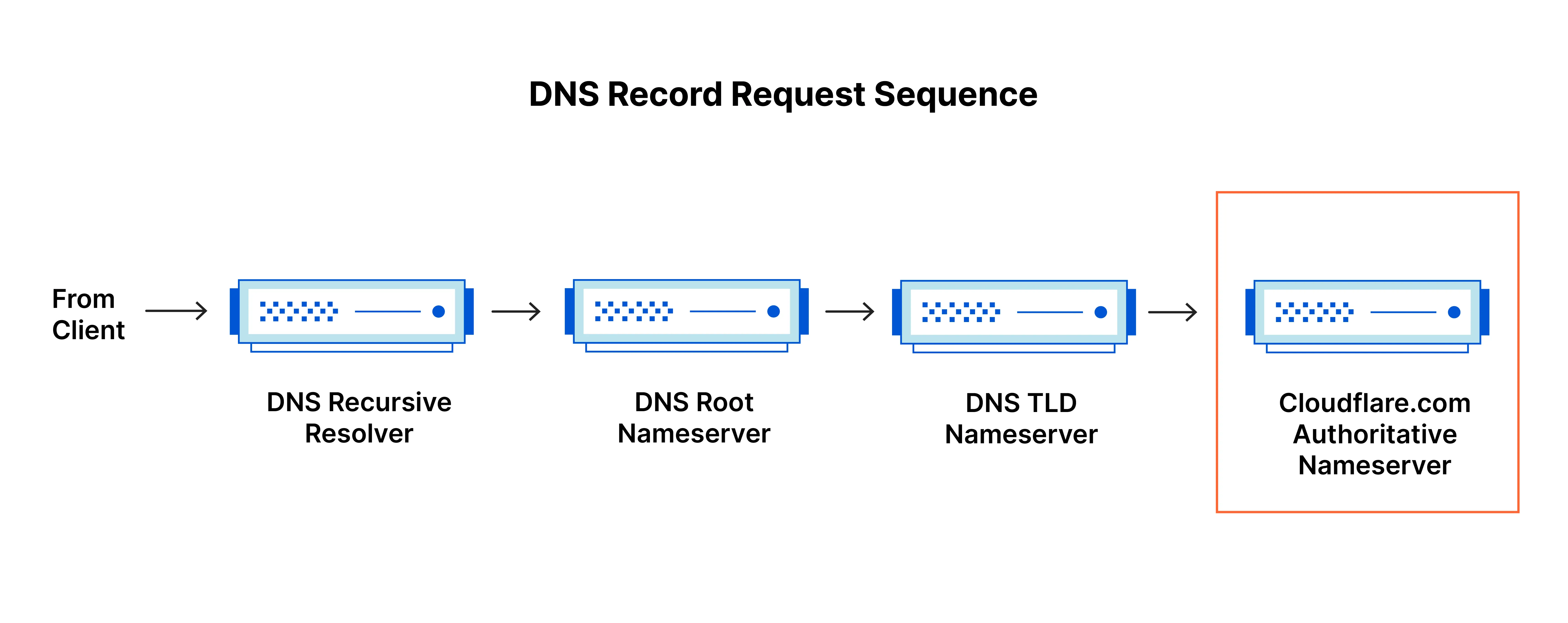
We can learn how this process works using an example. Lets assume you are trying to access a website using your browser. So in this example:
Client - your web browser
Requested website - www.xerxesviper.fyi
To being with when you enter the designate website in your browser -
The browser first checks its local DNS cache to check if this website has been visited before to avoid extra time delay for the DNS query. Assuming you are visiting the website for the first time, there starts the journey to fetch the associated IP address.
Once the browser finds a DNS cache miss, it then forwards the request to the recursive DNS resolver (first DNS server in the above image). The recursive resolver first checks its cache to see if it already has the IP address for the domain name. If the information is in the cache and is not expired (based on the TTL - Time To Live), it returns the IP address directly to the browser.
If, once again, there is a DNS cache miss, the recursive resolver then forwards the request to the Root nameserver (second DNS server in the image) by acting on behalf of the client to find the IP address associated with a domain name. The root zone is the top-level DNS zone in the hierarchical namespace of the DNS, acting as the single starting point for all DNS lookups. To remember - the root nameserver DOES NOT provide the IP address directly. Instead it directs the recursive resolver towards the associated TLD nameserver.
The root nameserver then directs the recursive resolver towards the TLD Nameserver. TLD (Top Lever Domain) the highest level in the hierarchical DNS of the internet and is the last segment of a domain name, the part that follows the final dot. For instance .com, .org, .xyz, .co.uk, .fyi, .vodka (yes its real) are all top level domains. In our example the root nameserver will direct the recursive resolver towards the .fyi TLD nameserver for our website. The TLD nameserver does not provide the final IP address either. Instead, it directs the recursive resolver to the authoritative nameserver for the specific domain
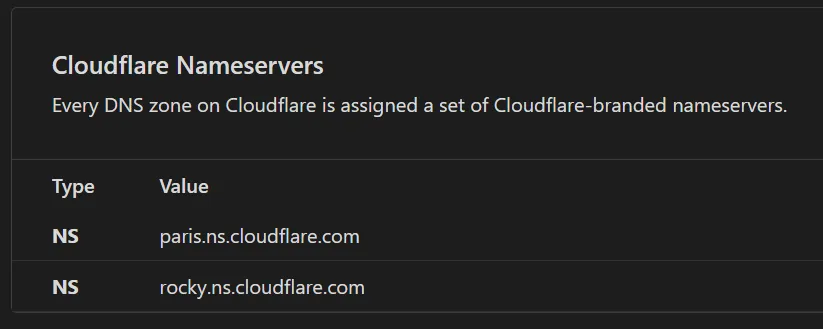
The TLD nameserver then directs the recursive resolver to the Authoritative nameserver of the domain, which in our case would be xerxesviper.fyi. These authoritative nameservers are typically provided by the entity that manages the DNS records for a specific domain. This can be the domain registrar, a DNS hosting provider, a webhosting provider, or a third-party DNS service provider. In our case as the website is hosted on Cloudflare, the authoritative nameservers are provided and maintained by Cloudflare as shown in the image below.
Finally, the recursive resolver send the DNS query to the authoritative nameserver which indeed provides the IP address for the requested website. So in our example the authoritative nameserver will provide the following:
- Query - www.xerxesviper.fyi
- Answer
- IPv4 = 104.21.22.87
- IPv6 = 2606:4700:3031::ac43
Finally your browser can now make a HTTP request to the IP address and the server at that IP will return the webpage to be rendered in your browser.
Now that we have an understanding of how DNS works, we can see how it is abused for fast flux.
How Fast Flux works?
The backbone of Fast Flux network is that multiple IP addresses can be associated to the same the same domain name. For example, a simple nslookup for www.google.com show that there are multiple IP addresses associated with the name as shown below:
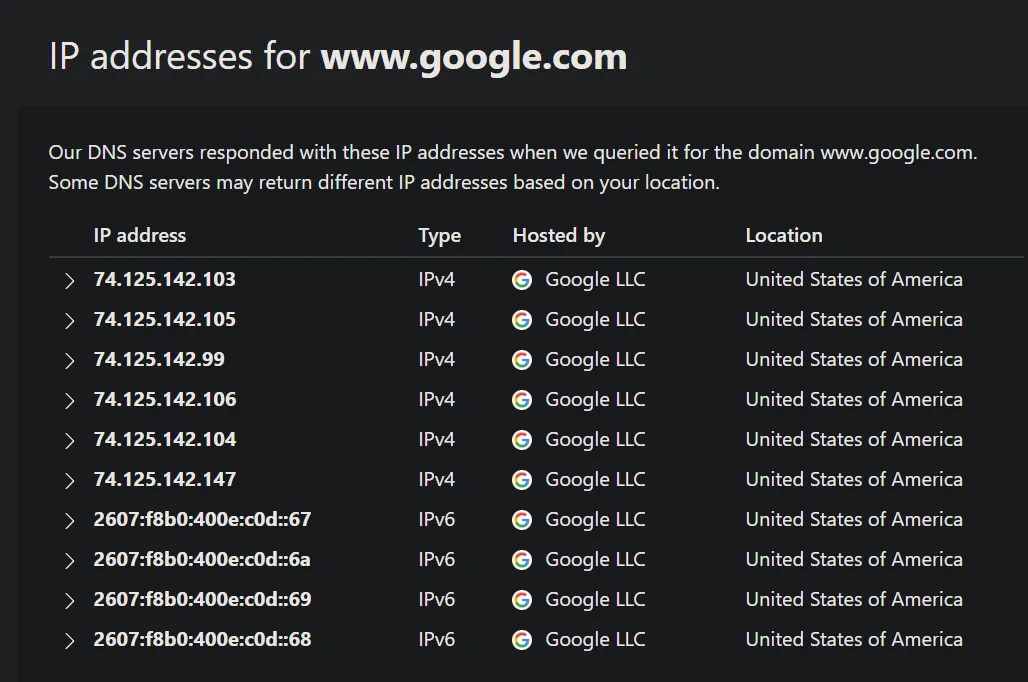
This exact this is the bread and butter of Fast Flux. Fast Flux involves associating multiple IP addresses with a single domain name and rapidly changing these IP addresses to evade detection and blocking efforts. These IP addresses are usually independent IPs, often those of compromised hosts involved in a botnet.
So lets see how a fast flux network works, assuming we already have a botnet ready for multiple IPs. If not, a botnet can be rented for pretty cheap prices on darknet.
The process starts with the registration of a domain name that will be used for malicious activities, often chosen to appear legitimate to deceive victims. This is generally done using Tyosquatting. The DNS records of this newly registered domain are then configured to use a short Time-to-Live (TTL) value, which determines how long a DNS record is cached by resolvers. This is done to make sure that the changes to the DNS records propagate quickly and the victim has to make a DNS request every time they want to access the site.
The botnet mentioned before makes a comeback here. The attackers control the botnet, which indeed is used to host the malicious content. Because there are multiple machines in this botnet - translating to multiple independent IPs, the IP address associated to the website in the DNS record in changed frequently.
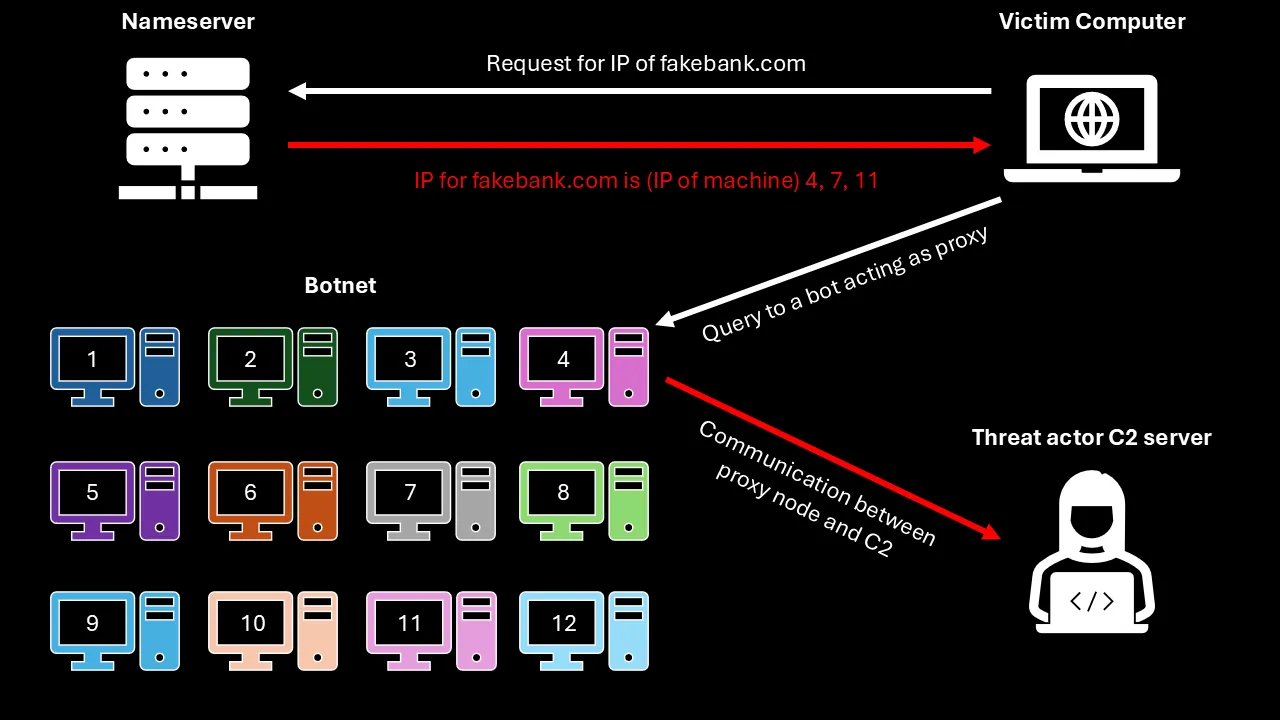
So how this works is that when the client/victim requests for the IP address of the fake/malicious website, the Authoritative nameserver (because of the very short TTL, ~160 seconds or less) send back a new IP address for the website. However, the client does not receive the actual IP address of the fake/malicious website, but the IP address of one of the many devices compromised under the botnet. These devices act as proxies between the client/victim and the command & control (C2) server of the cybercriminals. This rapid rotation of IP addresses provides load balancing and redundancy, ensuring that if one IP address is taken down or blocked, the domain can still resolve to other IP addresses, maintaining the availability of the malicious service. The technique makes it challenging for security researchers to track the source of the malicious activity, as traditional methods of blocking or taking down malicious domains become less effective. An example of this whole process is shown the image below. As you can see that the nameserver replies with IPs of machines 4, 7, and 11 in this case. These are the values that are constantly changed so that blocking one IP/machine does not affect the malicious campaign as whole.
Finally Fast flux comes in two flavours:
- Single-Flux: This involves rapidly changing the IP address of a single DNS A record, meaning that the IPv4 address associated with the domain name in the DNS record is constantly changes while the authoritative nameserver stays the same.
- Double-Flux: This involves rapidly changing the IP addresses of both the DNS A records and the NS (name server) records. This means that the IPv4 address, as well as the authoritative nameserver, is changed constantly, adding an additional layer of complexity.
Some FAQs
If my laptop is compromised and used in a botnet, then can my laptop IP (router IP) be used as the A record for fast flux?If your laptop becomes compromised and is part of a fast flux network, its IP address can indeed be used as part of the fast fluxing process.
Now that my laptop is part of fast flux network, if someone makes a DNS request for the malicious domain will my laptop then host the website?No, your laptop would not directly host the website. Instead, it would act as a proxy within the fast flux network, forwarding the DNS request to another compromised host that is actually hosting the malicious content.
Then in case my laptop is a compromised host in a fast flux network, it will act basically like a VPN server just without the encryption?Yes, that’s correct. In a fast flux network, your compromised laptop would act similarly to a VPN server but without the encryption. Indeed as a proxy node.
Can fast flux be done by buying off the shelf VPN subscription? If we just need a lot of IPs, VPN can provide that while also keeping the data encrypted, which is better for the attacker.Yes. Fast flux can be implemented by leveraging a large pool of IP addresses, which can be achieved by purchasing VPN subscriptions. And using a VPN for fast flux can provide additional security benefits, such as encryption, which can help protect the data being transmitted. However, this tends to be more expensive and suspicious, and is thus ignored by cybercriminals.

